Installation
Be sure to complete the prerequisites from Requirements before proceeding.
Particularly, make sure you have your data access credentials (e.g., IAM Role ARN for AWS EKS + S3) ready before going through the Agent Setup below.
Agent Setup
Robust Intelligence provides a self-guided installation process through the web client, which will automatically generate a pre-filled Helm values file for your agent based on your cloud configuration.
To begin, sign in to your Administrator account, navigate to the Organization Settings page, and click on the Manage Agent Setup tab.
From there, clicking on the Create Agent button will launch a modal that walks you through the self-guided installation.
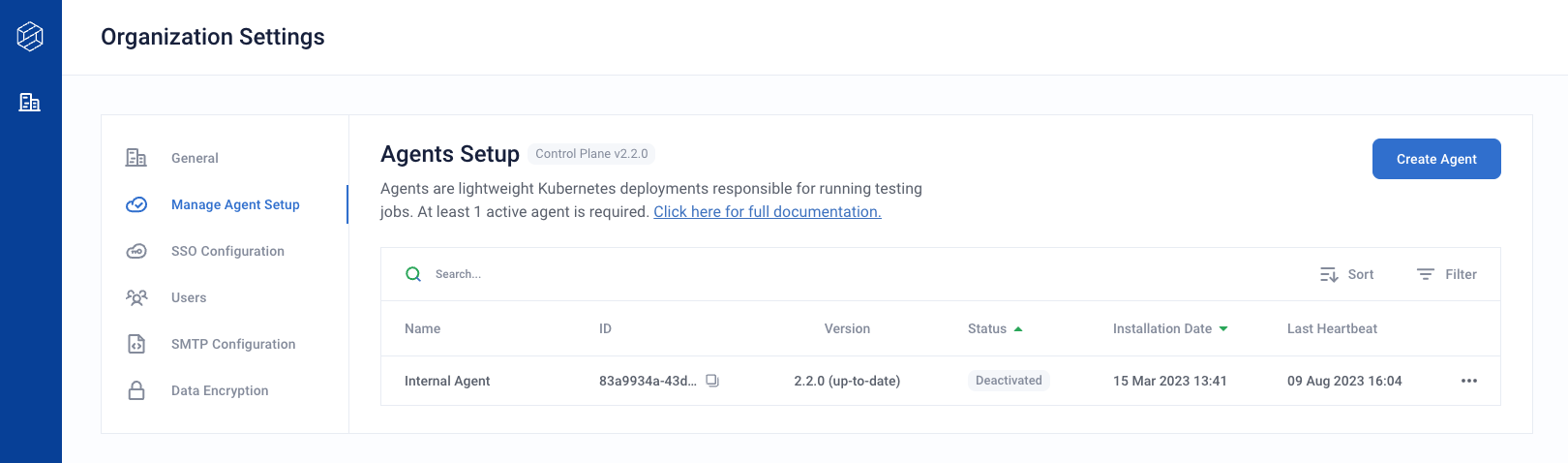
Select a unique name to identify your agent, and input the data access credentials generated during the Requirements phase.
Upon completing the setup, you will receive the following:
A pre-filled
*_values.yamlfile for therime-agentHelm chartHelm commands to install the chart
Helm Installation
Point your local
kubectlto your data plane K8s cluster and namespace.Execute the provided Helm commands to install the agent in your K8s cluster. They will look like this:
helm repo add robustintelligence https://robustintelligence.github.io/helm --force-update helm upgrade -i rime-agent robustintelligence/rime-agent \ --version $RI_VERSION \ --values $PATH_TO_VALUES_FILE
Validation
After performing the Helm installation, use the following reference to should smoke test your agent installation.
Infrastructure
Point your local
kubectlto your data plane K8s cluster and namespace.Inspect the Deployments. All containers should be ready.
> kubectl get deployments NAME READY UP-TO-DATE AVAILABLE AGE rime-agent-launcher 1/1 1 1 5m26s rime-agent-operator-controller-manager 1/1 1 1 5m26s rime-agent-rime-cross-plane-server 1/1 1 1 5m26s
Web Client
The status of the agent is regularly updated on the Agents Setup page of Organization Settings (as well as the Agent Status page of Workspace Settings).
Verify that the new agent has a status of
Activein the web client.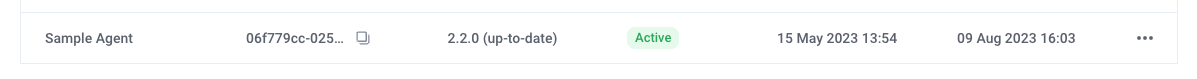
Make note of the new agent’s ID, as you will need to reference it for the other steps.
Connect the agent to at least one Workspace via the Workspace Agent Configuration steps.
Python SDK and REST API
The following commands should each return a list of the agents currently assigned to your Workspace. Be sure to use an API Token from a Workspace that you connected to the new agent.
Verify that the outputs of the commands contain a uuid matching that of the newly-deployed agent.
- Python SDK
from rime_sdk import Client rime_client = Client("rime.<DOMAIN>.com", "<API_TOKEN>") [print(x) for x in rime_client.list_agents()]
{'agent_id': {'uuid': ... }
- REST API
curl -X GET 'rime.$DOMAIN.com/v1/agents' \ --header "rime-api-key: $API_TOKEN" \ --header "Content-Type: application/json"
{"agents":[{"agentId":{"uuid:": ... }%
Monitoring Setup (optional)
You may optionally install the rime-extras helm chart which provides system/application monitoring via the Datadog Agent and Prometheus Node Exporter.
Helm Installation
Point your local
kubectlto your data plane K8s cluster and namespace.Create a
values.yamlfile enabling the Datadog Agent and Prometheus Node Exporter:rimeExtras: # -- Whether to install the DataDog Agent datadog: true # -- Whether to install the Prometheus Node Exporter prometheusNodeExporter: true
Execute the below Helm commands to install the chart in your K8s cluster:
helm repo add robustintelligence https://robustintelligence.github.io/helm --force-update helm upgrade -i rime-extras robustintelligence/rime-extras \ --values $PATH_TO_VALUES_FILE
Log Archival Setup (recommended)
For convenient debugging, you can configure the agent to capture logs for failed jobs. Once enabled, the log archival feature automatically uploads failed job logs to your AWS S3 bucket, which can then be consumed via the Python SDK or REST APIs (see Fetching Test Run Logs for more details).
While log archival has been designed for AWS, it can also be configured to work with Azure or GCP storage. For help setting up with Azure or GCP, contact the Robust Intelligence solutions team.
Helm Installation
If you manage your Robust Intelligence agent installation via Helm, follow the instructions below.
- Collect the following information:
- The IAM Role for the agent.
This can be found under
rimeAgent.operator.modelTestJob.serviceAccount.annotations.eks.amazonaws.com/role-arn.Create the role now if it does not exist. See Data Access Permissions.
- The name of the Service Account used for the operator controller manager (default is
rime-agent-operator). Run
kubectl -n <namespace> get podsand find the pod name for the operator. The name should be similar torime-agent-operator-controller-manager.Run
kubectl -n <namespace> describe pod <pod_name> | grep 'Service Account:'to locate the Service Account name.
- The name of the Service Account used for the operator controller manager (default is
- The ARN of the S3 bucket where you want logs to be uploaded. Note: The S3 bucket must be in the same region as the EKS cluster.
We recommend using the default S3 bucket made during the initial installation.
Logs will be stored in a /logs folder.
Expand the trust relationship of the agent’s IAM Role to include the Service Account of the operator controller manager.
// TRUST RELATIONSHIP OF AGENT IAM ROLE { "Version": "2012-10-17", "Statement": [ { ... "Condition": { "StringEquals": { "oidc.eks.region-code.amazonaws.com/id/EXAMPLED539D4633E53DE1B71EXAMPLE:sub": [ ... "system:serviceaccount:$AGENT_NAMESPACE:$AGENT_OPERATOR_SERVICE_ACCOUNT" ] } } } ] }
Create a new IAM Policy with permissions that allow for management of log files.
// PERMISSION POLICY FOR LOG ARCHIVAL { "Version": "2012-10-17", "Statement": [ { "Sid": "LogArchivalAccessBucket", "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "<BUCKET_ARN>" ] }, { "Sid": "LogArchivalAccess", "Effect": "Allow", "Action": [ "s3:GetObject", "s3:DeleteObject", "s3:PutObject" ], "Resource": [ "<BUCKET_ARN>/logs/*" ] } ] }
Attach this policy to the agent IAM Role.
Go to the
values.yamlfor your rime-agent deployment and set the following values:rimeAgent: operator: serviceAccount: annotations: eks.amazonaws.com/role-arn: <ROLE_ARN> logArchival: enabled: true storageBucketName: <S3_BUCKET_NAME> endpoint: "s3.amazonaws.com" type: "s3"
Run
helm installorhelm upgrade. You may also need to manually restart the operator to refresh its AWS credentials.
Your log archival setup is complete. See Fetching Test Run Logs to learn how to retrieve logs.
